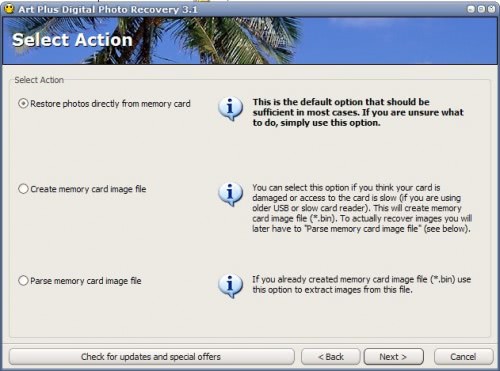
Except for fans, the typical hard drive is just about the only piece of a modern computer that still has moving parts. While solid state drives are becoming more popular every day, most of us still use at least one regular hard drive, spinning platters and all. Because those platters are spinning around at 5400 or 7200 PRM (and sometimes even faster) for countless hours, you would do well to check on their health every now and then.
Also, even if your hard drive is perfectly healthy, it may still pose a performance bottleneck on your system: Reading and writing files to a regular hard drive are two of the slowest operations computers have to do these days. So how can you tell if your hard drive is healthy, and how can you tell how fast it is?
Health: CrystalDiskInfo
![hard-drive[5] healthy hard drive](http://main.makeuseoflimited.netdna-cdn.com/wp-content/uploads/2012/03/hard-drive5.png?323f2c)
First things first – let’s start with health. CrystalDiskInfo is a free tool, which we’ve mentioned more than three years ago. Well, it is still around, and it is still an excellent tool. It is under constant development, with the latest version released early March. CrystalDiskInfo lets you see a wealth of information about your hard drive, using the drive’s S.M.A.R.T self-monitoring interface. For example, we can see that the hard drive above (the newest drive in my system) has been operating for 4,411 hours, which are 183 days – during which I restarted my computer 28 times. This is an interesting bit of trivia, but it also lets you estimate how close your drive is to failure: many vendors specify something called “MTBF”, or “mean time before failure” for their hard drive.
Another important metric you can see above is the drive temperature, 43 degrees Celsius (if you prefer Fahrenheit, CrysalDiskInfo can do that too). Much like the MTBF, this information can be used to estimate how well your drive is doing: I searched for the specifications of this hard drive (WD20EARX), and found them on the Western Digital website. WD specifies an operation temperature of 0 to 60 degrees Celsius for this drive, so now I know I’m in range (albeit on its high end).
Other measurements are very technical, but fortunately, CrystalDiskInfo makes life easy by just stating that the drive’s health status is good.
Speed: DiskBench

Now that you know how healthy your hard drive is, it’s time to find out how fast it is, and this is what DiskBench does. Unlike CrystalDiskInfo, DiskBench does not contain large color-coded buttons and indicators: You get five very businesslike tabs, and that’s it. Each tabs lets you run a different sort of test on your drive. Above you can see the batch file creation test: This test rapidly creates a number of files, and shows you how long each operation took.
There is one very important thing you should watch for when using DiskBench: As you can see above, the application lets you change the block size used for creating files. For some crazy reason, it also lets you specify block size in gigabytes (GB). When I first started testing DiskBench, I mistook this setting for file size rather than block size, and set it to 2 GB. My computer completely choked – I haven’t seen Windows 7 become stuck so badly in a very long time. I was unable to run Task Manager or do anything else for over fifteen minutes, and ended up hard-booting the computer. Scary.
So again: Block size is not like file size. If you want larger file, you should increase the number of blocks (“Initial number of blocks” and “Block increase” in the particular test above).
That said, DiskBench provides interesting metrics, and can let you decide where you want to place page files and other important files.
Suggest Other Free Benchmarking Tools
When you want to gauge your hard drive’s health, what do you use? Have you made the leap to an SSD yet?
Source:- makeuseof